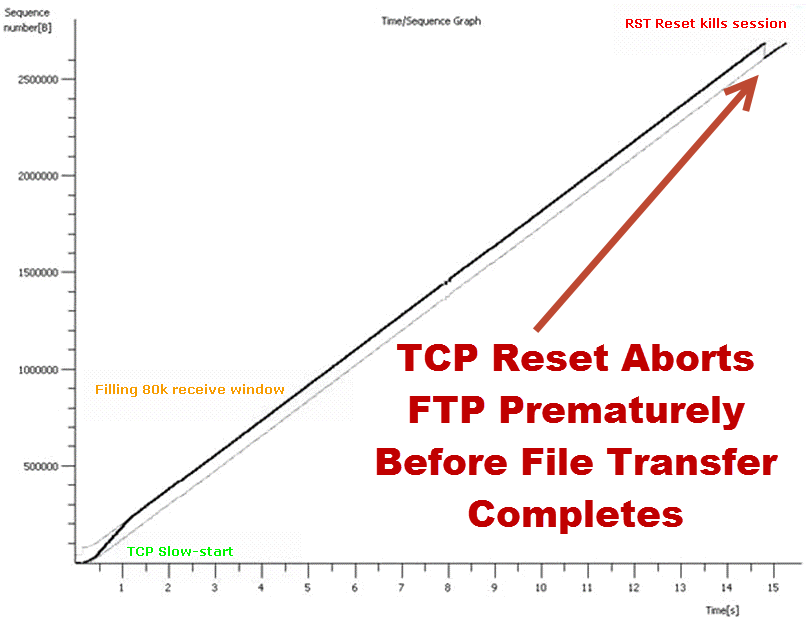
This TCP sequence graph uncovers a network anomaly where high-stakes file transfers are prematurely terminated due to unexpected TCP Resets. Despite initial smooth progression, akin to the creative workflows in a Mad Men era, our modern-day digital transfer is disrupted—not by cigarettes and old-fashioned vices, but by a digital hiccup that could spawn a plot twist worthy of Don Draper’s most challenging ad campaigns. The graph marks the tragic end of FTP sessions, akin to the abrupt cutoff of a 1970s television signal, with TCP Resets acting as the invisible antagonist.
In a network mystery with high visibility akin to an ad firm’s peak season rush, the issue at hand is not a lack of creative direction but a technological misfire where each aborted transfer is a missed deadline. The clue? A TCP Reset, a digital ‘no’ in a world that demands ‘yes.’ The twist? Packets captured at strategic test points reveal an internal MITM—our own security device in disguise, issuing Resets from both ends. The culprit exposed not by a smoking gun, but by incongruent Hop Counts and IP Fragment IDs, unmasking a Linux IPTABLES Firewall as the unexpected interloper in this tale of digital intrigue.
Just as Don Draper would pivot to meet a market challenge, the network team, with forensic precision and a touch of digital sleuthing, navigates away from open-source firewalls towards a more stable solution, much like swapping a risky ad pitch for a tested slogan. The stakes are high, the data critical, and the solution—a change in the network’s very infrastructure—mirrors the transformative steps an ad agency might take to evolve with the times. This graph is not just a network analysis; it’s a storyline of adaptation and resolution in the face of technological adversity.
Don Draper and the Case of the Digital Detective: Solving the Mystery of the Mischievous Network
Imagine Don Draper, the dashing ad man from “Mad Men,” transported into our era, a cigarette in one hand and a martini in the other, squinting at a computer screen displaying a baffling network failure. This is the scene at an advertising agency where high-stakes digital drama unfolds, threatening the delivery of media to top-tier clients. Would Don charm his way through the bytes and bits, or would he need something stronger than his usual scotch?
In this digital age, unlike the smoke-filled offices of Sterling Cooper, the lifeline of creativity flows through cables and clouds. When the network at this agency went kaput, my client, unlike our fictional Mr. Draper, didn’t resort to liquid lunches for solutions. They had a backup plan straight out of a 1960s playbook – shipping DVDs and hard drives by air, just shy of strapping them to carrier pigeons!
As a seasoned network sleuth, I’ve navigated through the murky waters of cyber threats, resurrected communications at the Pentagon post-9/11, and ventured into war-torn lands to untangle digital dilemmas. So, this network conundrum was more of a “Tuesday” for me.
The Plot Thickens
Here’s the twist: some file transfers were pulling a Houdini, vanishing mid-way. Not all, mind you, just a select few that enjoyed the thrill of the incomplete journey. This wasn’t just a network problem; it was a digital whodunit.
Unraveling the Technological Tango
The first clue lay in the mysterious TCP Resets, like unexpected plot twists in a Hitchcock thriller. These resets were cutting off file transfers like a bad movie edit. The question was: who was yelling “cut!”? In the style of any good detective story, we looked for suspects. Was it a rogue firewall playing vigilante? Or perhaps a mischievous man-in-the-middle, a digital Moriarty of sorts?
After some digital sleuthing worthy of Sherlock Holmes himself, we pinpointed the culprit: a Linux IPTABLES Firewall with a penchant for drama. It was like discovering the butler did it, but in this case, the butler was a bunch of code on a mission to disrupt.
A Finale Worthy of Mad Men
Replacing the open-source firewall with a Cisco PIX turned our thriller into a feel-good movie. The network was back, file transfers were completing, and the security manager, who almost took a metaphorical leap from the rooftop of despair, was back on solid ground.
In a parallel universe where Don Draper navigates the digital age, this episode might end with a triumphant ad campaign and a wild office party, complete with witty banter and clinking glasses. In our world, the celebration was more subdued but equally satisfying. We might not have had the glamour of “Mad Men,” but we had the thrill of cracking a case that would make even Don raise his glass in salute.
In the end, this adventure was less about cigarettes and scotch and more about packets and protocols. But who says network forensics can’t have a bit of Mad Men flair?