On The Wire
Welcome to “On the Wire” at the Security Institute, where we dissect the intricacies of IT leadership and the art of cybersecurity. This blog serves as your compass in the ever-shifting landscape of digital defense, exploring a panorama of topics from the strategic to the technical. Join us as we unravel the threads of cybersecurity, offering insights and guidance on cultivating a resilient, breach-free future through the Certified Enterprise Zero Day Badge Program. Whether you’re an emerging IT leader or a seasoned security veteran, “On the Wire” is your beacon for thought leadership, innovative strategies, and the pursuit of excellence in cybersecurity.
Exploring Web Vulnerabilities with DVWA: Setting Up Your Virtual Playground
In the dynamic realm of cybersecurity education and testing, having a secure environment to explore vulnerabilities is crucial....
Reading PCAPs with Wireshark Statistics: Enhancing Network Analysis
In the dynamic realm of network analysis and cybersecurity, interpreting packet captures (PCAPs) can often feel like navigating...
Unlocking Cybersecurity Insights: Mapping IP Addresses with Wireshark’s GeoIP Feature
In today's rapidly evolving cybersecurity landscape, the ability to trace the origins of network traffic isn't just...
Pentagon 911 Communications Recovery
IntroductionIn the wake of the 9/11 Pentagon disaster, organizations faced unprecedented challenges in restoring vital IT...
ERSPAN for Security Incident Response
IntroductionPurpose: The case study highlights a Wireshark Wednesday event, focused on exploring the ERSPAN (Encapsulated Remote...
ERSPAN Case Study
IntroductionPurpose: This case study focuses on the implementation of ERSPAN technology, a remote network monitoring solution,...
DigiCert Revocation Case Study
IntroductionIn an era of increasing cyber threats, organizations are under constant pressure to safeguard their networks against...
Fostering Innovation and Growth: Collaboration, Mentorship, and Leadership at SecurityInstitute.com
At SecurityInstitute.com, we are more than just a cybersecurity platform; we are a vibrant think tank where innovation,...
Unlock the Future of Cybersecurity with Our Zero Day Badge Bundle
In today's fast-paced digital landscape, the stakes are higher than ever. As cyber threats evolve, so must the skills and...
Unlock the Power of Wireshark Security Forensics with Our L1/L2 Assessment Badges
In today’s rapidly evolving digital landscape, the demand for cybersecurity professionals with specialized skills is at an...
Fortify Your Cybersecurity Skills with the SolarWinds Supply Chain Badge
In the constantly evolving landscape of cybersecurity, new threats emerge daily, and the security of supply chains has become a...
Security Institute: Your Gateway to Cybersecurity Mastery
In today’s ever-evolving digital landscape, cybersecurity professionals are tasked with the critical responsibility of...
Mastering Network Traffic Analysis with Wireshark: A Guide to Effective Filtering
Few tools in cybersecurity and network management match Wireshark's prowess and depth. This open-source network protocol...
Highlighting the Value of Popular Cybersecurity Certifications and Our Unique Expertise
In the rapidly evolving field of cybersecurity, industry-recognized certifications are essential for professionals looking to...
Analyzing Network Traffic and Response Times with the Time Column in Wireshark
In the realm of network analysis and cybersecurity, Wireshark stands tall as a vital tool for dissecting the complexities of...
How to Use Name Resolution in Wireshark to Enhance Packet Analysis
In the world of network analysis, understanding packet captures is crucial for diagnosing issues, optimizing performance, and...
Unlocking Cybersecurity: Advanced File Extraction from PCAPs with Wireshark
Welcome back to the Wireshark Master Class! In the intricate world of network analysis and cybersecurity, the ability to extract...
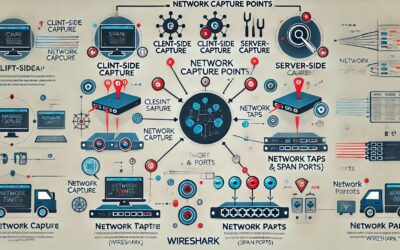
Unleashing Network Insights: Mastering Wireshark’s Capture Points
Welcome to another insightful lesson in our Wireshark tutorial series! Today, we're delving deep into a critical aspect of...
Unleashing Network Insights: Mastering Wireshark’s Command Line Tools
In cybersecurity and network diagnostics, efficiency and precision are everything. Whether you're a seasoned network...
Unveiling the Power of Wireshark: Your Gateway to Mastering Network Traffic Analysis
In today's interconnected digital landscape, comprehending network traffic is not just advantageous—it's essential. From...
Mastering Wireshark: Your Gateway to Network Mastery
In today’s interconnected world, where digital interactions shape every aspect of our lives, navigating and understanding...
Protecting Against the Unknown: Our Zero-Day Prevention Strategy
Bill Alderson's Proactive Approach to Cybersecurity: Thwarting Zero-Day AttacksIn today's digital age, cybersecurity is not just...
The Cybersecurity Battle: Innovation, Human Error, and the Fight for Digital Integrity
Bill Alderson's Insights: Transforming Cybersecurity from Reaction to PreventionIn the vast and intricate landscape of...
Minimizing Your Digital Footprint: The Attack-Surface Badge Program
IntroductionIn the realm of cybersecurity, understanding the "attack surface" of a system is crucial. This concept refers to all...
Understanding TCP-QUIC Protocol: A Comprehensive Guide
IntroductionIn the ever-evolving landscape of internet protocols, the introduction of TCP-QUIC stands as a significant...
Mastering Wireshark for Enhanced Cybersecurity: A Comprehensive Guide
In the digital age, cybersecurity is not just a necessity but a critical component of any organization's IT infrastructure. With...
Embark on a Journey of Advanced Cybersecurity Mastery at the Security Institute Think Tank
"Education is the passport to the future, for tomorrow belongs to those who prepare for it today with diligence and passion." -...
Paul Barrett
Paul Barret: NetScoutPioneering Network Assurance and Cybersecurity - A Journey of Innovation and LeadershipPaul Barrett boasts...
Jon DiMaggio
Jon DiMaggio is a highly accomplished cybersecurity professional and published author. He currently holds the position of Chief...
Gary Hayslip: Chief Security Officer and Cybersecurity Expert
Gary Hayslip: An Experienced Global CISO and proven Cybersecurity ProfessionalGary Hayslip's professional journey affirms his...
Colonel David Wills: A Journey of Military Excellence and Strategic Leadership
Colonel David WillsColonel (COL) David Wills, retired from the U.S. Army in 2021 after serving as the Deputy Director for C4...
Brian Clinkenbeard
Brian Clinkenbeard: Virtual CISO and Inventor of new and innovative approaches and methods for CybersecurityPioneering Data...
Betty DuBois: Packet Analyst and Network Troubleshooting Expert
Betty Dubois: Chief Detective at Packet DetectivesBetty DuBois, the Chief Detective at Packet Detectives, a network performance...
Len Shustek: Technologist, Educator, and Computing History Steward
Computer science has its fair share of extraordinary individuals who have left an indelible mark on the industry. Leonard J....
Dr. Harry J. Saal: Visionary Technologist, Entrepreneur, and Philanthropic Leader
Dr. Harry J. Saal BiographyDr. Harry J. Saal, a distinguished American technology entrepreneur, executive, and philanthropist,...
Radia Joy Perlman: Pioneering Secure Protocols and Shaping the Future of Networking
Radia Joy Perlman: Pioneering the Future of Technology with Vision and Expertise.Few names resonate with as much influence and...
Vinton Cerf: Internet Pioneer Advocating Privacy and Security Excellence
Vinton G. Cerf: Father of the Internet and a Tech Visionary.Vinton “Vint” G. Cerf is vice president and Chief Internet...
The Frontline of Network Defense: Shifting from Response to Prevention with Zero-Day Strategies
In the ever-evolving digital landscape, where the boundaries between the virtual and the real are increasingly blurred, there...
Learn Zero-Day Threat Prevention Strategies With Security Experts
In a time where digital threats loom larger than ever, the need for cutting-edge cybersecurity strategies is critical. The...
Web3 NFT Crypto Community Membership
Crypto Fundamentals Bitcoin vs. EthereumCybersecurity professionals need to understand Bitcoin’s network and development focus....