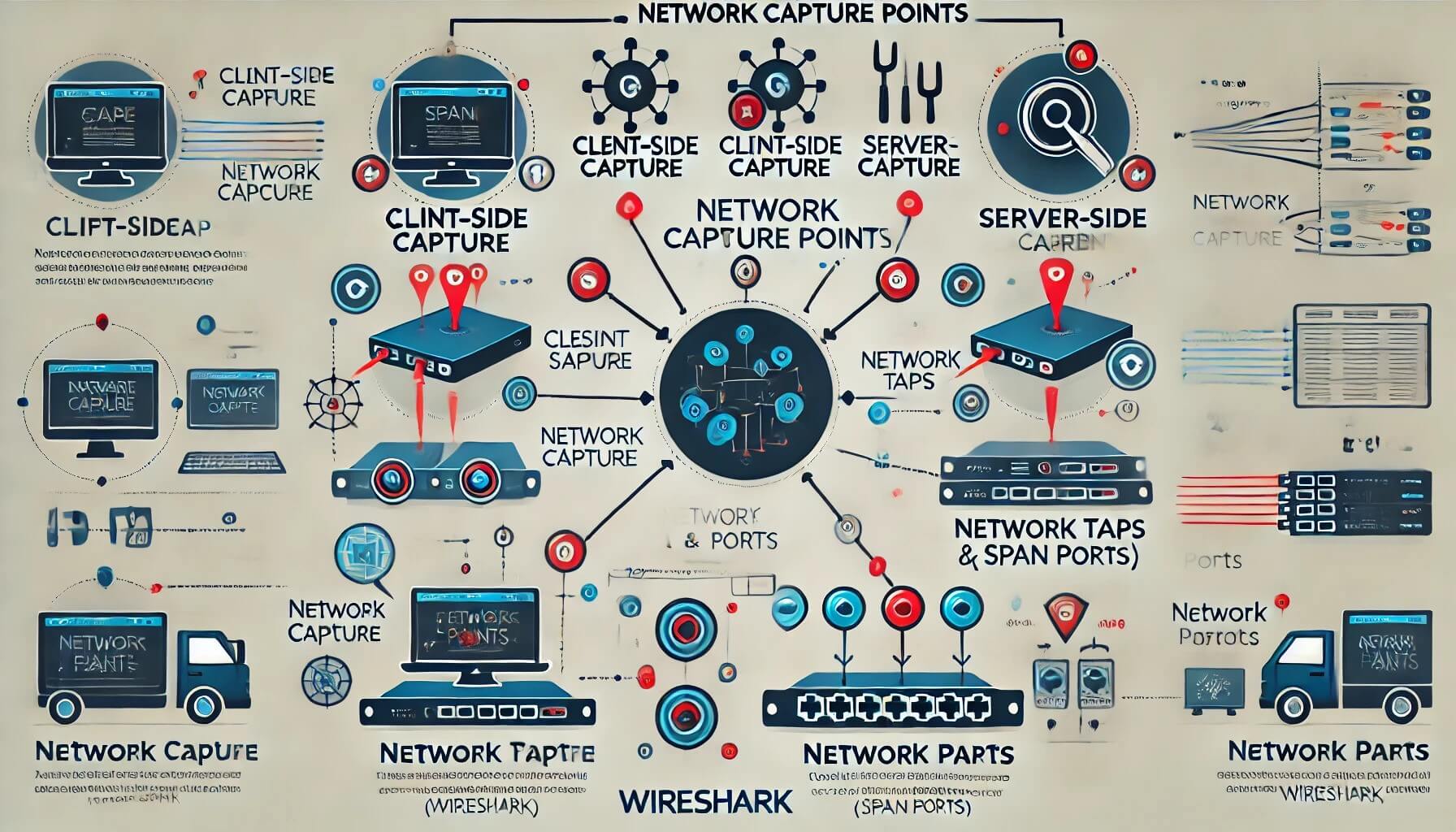
Welcome to another insightful lesson in our Wireshark tutorial series! Today, we’re delving deep into a critical aspect of network diagnostics: where and how to capture network packets effectively using Wireshark. Whether you’re a seasoned network administrator troubleshooting complex issues or a curious enthusiast diving into packet analysis, understanding the optimal capture points can significantly elevate your ability to diagnose and resolve network problems.
Defining the Problem: Key to Effective Capture
Before we explore where to capture packets, it’s crucial to define the problem clearly. Network issues vary widely—from intermittent connectivity problems affecting individual clients to widespread security incidents impacting entire networks. The nature of your situation will dictate where you should deploy Wireshark for optimal insights.
Client-Side Insights: Capturing from the Edge
Let’s start by considering scenarios where troubleshooting involves client-side issues. Imagine several users intermittently experiencing connectivity glitches while accessing a critical application. In such cases, capturing packets from the client side provides invaluable insights into the dynamics of traffic that directly impact user experience.
Installing Wireshark directly on the client device or capturing it at the access point where clients connect to the network allows you to observe real-time traffic patterns and pinpoint user session issues. This approach helps diagnose connectivity problems and provides visibility into how network conditions impact application performance from the end-user perspective.
Challenges of Server-Side Capture
While capturing packets from client devices offers immediate insights into user experience, server-side capture presents a different set of challenges. Access constraints, especially in cloud environments or virtual networks, often limit direct packet capture opportunities.
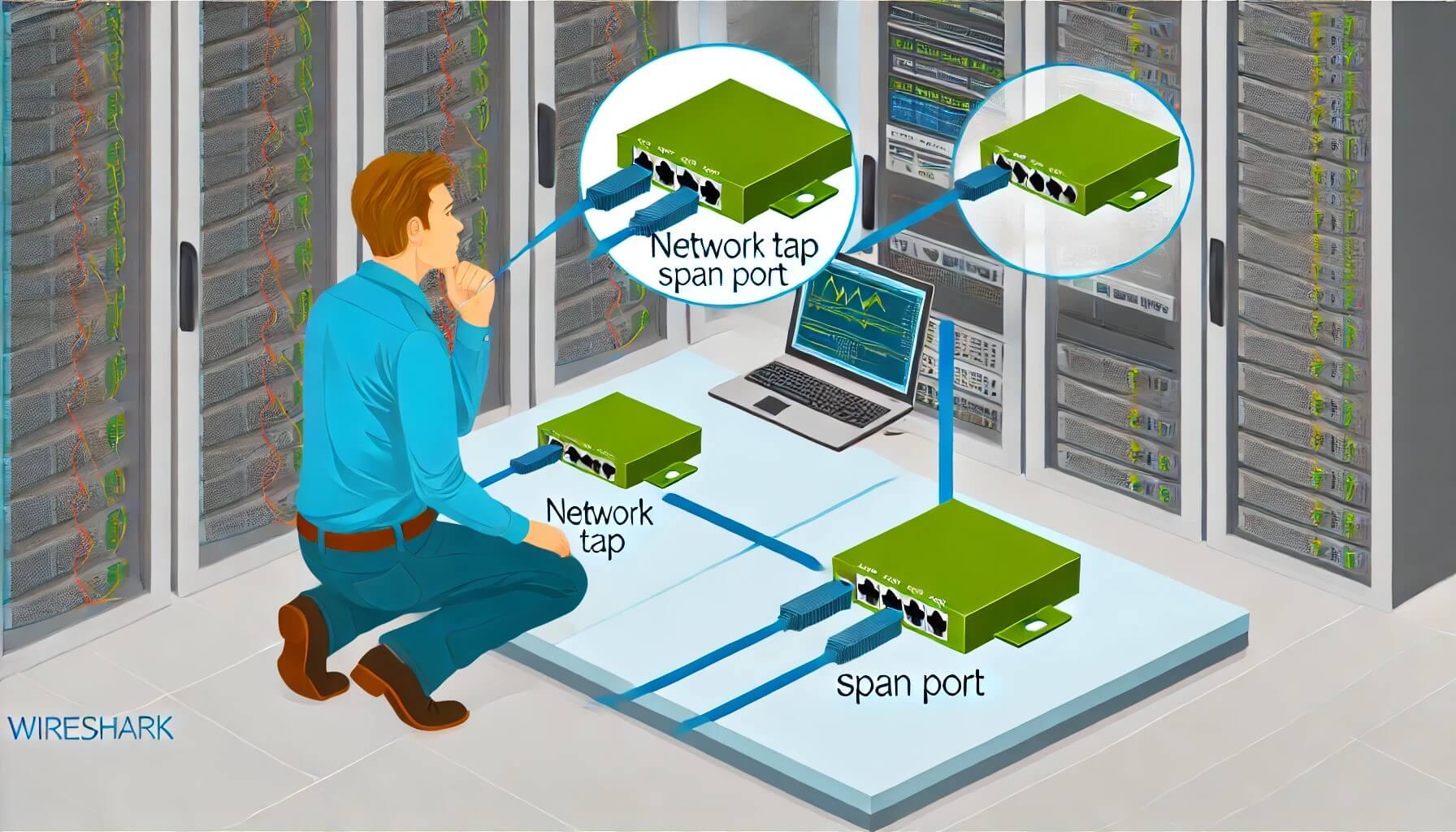
For instance, if your application servers are hosted in a cloud environment or within a managed data center, gaining access to the physical or virtual network infrastructure required for packet capture can be complex. In such cases, network administrators must rely on alternative methods like configuring SPAN (Switched Port Analyzer) ports or using network taps strategically placed within the network architecture.
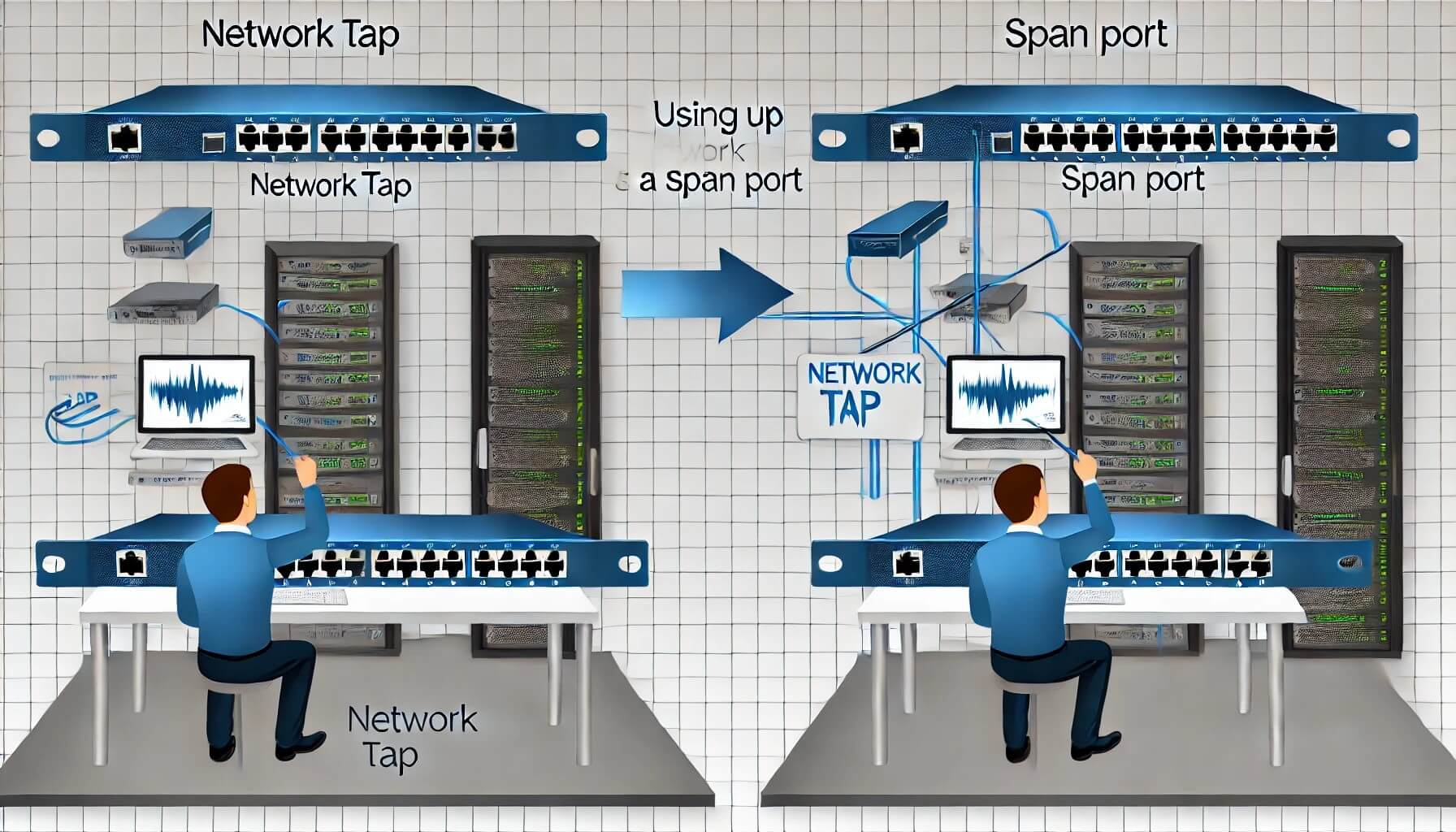
Optimal Capture Methods: Taps vs. SPAN Ports
Network Taps: Network taps remain the gold standard for thorough packet capture. These physical devices are designed to passively intercept and duplicate network traffic without disrupting the flow. By inserting a tap in line with the network connection, you can capture every incoming and outgoing packet without introducing latency or affecting network performance. Network taps are ideal when comprehensive visibility into network traffic is essential, such as troubleshooting intermittent issues or conducting in-depth security audits.
SPAN Ports: In environments where deploying physical taps isn’t feasible due to logistical or budgetary constraints, SPAN ports provide a viable alternative. SPAN ports, available on managed switches and routers, allow you to mirror traffic from one or more source ports to a designated monitoring port. Wireshark can then capture this mirrored traffic on a connected monitoring device or server. While SPAN ports offer flexibility and scalability, they require careful configuration to capture all relevant traffic accurately.
Practical Alternatives: Installing Wireshark on Clients
In scenarios where physical access to network infrastructure or SPAN capabilities isn’t available, installing Wireshark directly on client devices offers a practical solution. While this approach adds some overhead to the client’s resources and network interface, it provides real-time visibility into traffic patterns and application interactions from the client’s perspective.
Installing Wireshark on client devices allows network administrators to capture packets as they traverse the network interface, providing insights into specific issues affecting individual users or devices. This method is beneficial for troubleshooting client-specific connectivity issues or identifying anomalies in application behavior from the user’s endpoint.
Strategic Capture Point Selection
The ultimate goal of packet capture is to gain comprehensive visibility into network traffic dynamics. Ideally, network administrators should aim to capture packets simultaneously from client and server perspectives. This dual approach enables detailed analysis of end-to-end communication patterns, including TCP handshakes, response times, and backend interactions.
By capturing packets from multiple vantage points within the network architecture, you can correlate network events and identify potential bottlenecks or anomalies affecting overall network performance. This holistic view allows for more informed decision-making when troubleshooting network issues or optimizing network infrastructure.
Conclusion: Enhance Your Network Diagnostics
Mastering Wireshark’s capture points empowers network administrators and security professionals to unravel complex network issues precisely. Strategic capture point selection is crucial whether you’re troubleshooting user connectivity problems, investigating security incidents, or optimizing network performance.
By deploying Wireshark at the right capture points—whether on client devices, at network access points, or through SPAN ports—network administrators can gain actionable insights into network behavior, diagnose issues efficiently, and implement targeted solutions to enhance overall network reliability and security.
Ready to Explore Further?
Delve deeper into network diagnostics and master the art of packet analysis with Wireshark. Stay tuned for more insights, tips, and tutorials to elevate your networking prowess.